-
Notifications
You must be signed in to change notification settings - Fork 36
[User Guide] Starter Module Terraform Complete
The complete starter module provides full customization of the Azure Landing Zone using the config.yaml file. The config.yaml file provides the ability to enable and disable modules, configure module inputs and outputs, and configure module resources.
A custom config.yaml file can be passed to the configuration_file_path argument of the ALZ PowerShell Module. This allows you to firstly design your Azure Landing Zone, and then deploy it.
If not specified, the default config.yaml file will be used, which can be seen here.
Example input files can be found here:
- inputs-azure-devops-terraform-complete.yaml
- inputs-github-terraform-complete.yaml
- inputs-local-terraform-complete.yaml
The following table describes the inputs required for the complete starter module.
| Input | Placeholder | Description |
|---|---|---|
configuration_file_path |
<configuration-file-path> |
This is the absolute path to the configuration file. E.g. c:\my-config\config.yaml or ~/my-config/config.yaml. For YAML on Windows you will need to escape the \, i.e. c:\\my-config\\config.yaml. |
default_postfix |
<postfix> |
This is the default postfix used for resource names. |
The config.yaml file also comes with helpful templated variables such as starter_location and root_parent_management_group_id which get prompted for during the ALZ PowerShell Module run. Alternatively, you can opt to not use the templated variables and hard-code the values in the config.yaml file.
Note: We recommend that you use the
caf-enterprise-scalemodule for management groups and policies, and thehubnetworkingmodule for connectivity resources. However, connectivity resources can be deployed using thecaf-enterprise-scalemodule if you desire.
The schema for the config.yaml is documented here - Configuration YAML Schema.
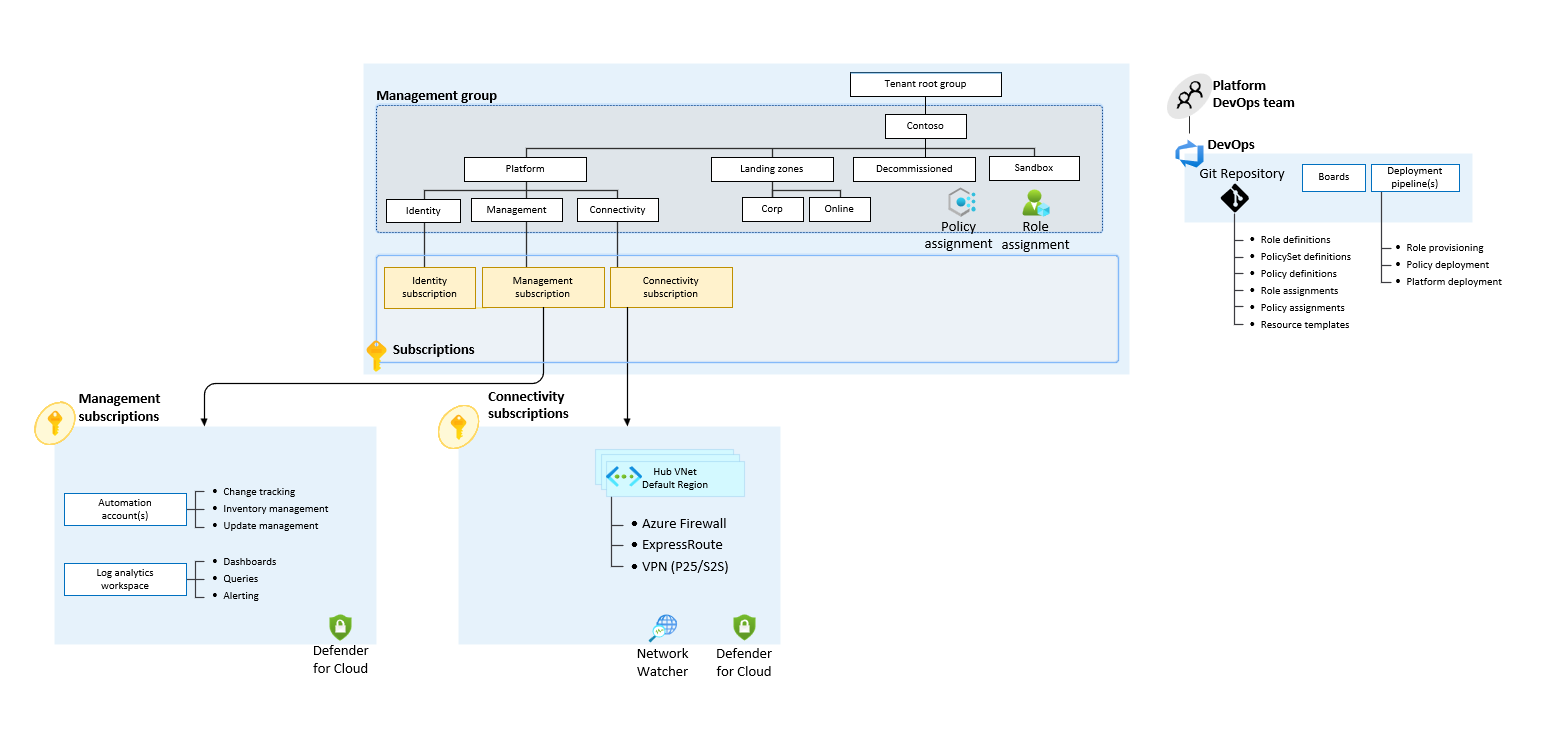
The caf-enterprise-scale module is used to deploy the management group hierarchy, policy assignments and management resources. For more information on the module itself see here.
The hubnetworking module is used to deploy connectivity resources such as Virtual Networks and Firewalls.
This module can be extended to deploy multiple Virtual Networks at scale, Route Tables, and Resource Locks. For more information on the module itself see here.
The avm-ptn-vnetgateway module is used to deploy a Virtual Network Gateway inside your Virtual Network. Further configuration can be added (depending on requirements) to deploy Local Network Gateways, configure Virtual Network Gateway Connections, deploy ExpressRoute Gateways, and more. Additional information on the module can be found here.
The avm-ptn-vwan module is used to deploy a Virtual WAN. Further configuration can be added (depending on requirements) to deploy VPN Sites, configure VPN Connections, and more. Additional information on the module can be found here.
Create a custom yaml config to tailor to your needs, for example an Azure Landing Zone with a three-region mesh:
- Example config file for hub and spoke: config-hub-spoke.yaml
- Example config file for Virtual WAN: config-vwan.yaml
This wiki is being actively developed
If you discover any documentation bugs or would like to request new content, please raise them as an issue or feel free to contribute to the wiki via a pull request. The wiki docs are located in the repository in the docs/wiki/ folder.

- Home
-
User guide
- Getting started
- Quick Start
- Starter Modules
- Input Files
- Azure DevOps Bicep Complete
- Azure DevOps Terraform Complete Multi Region
- Azure DevOps Terraform Sovereign Landing Zone
- Azure DevOps Terraform Basic
- Azure DevOps Terraform Hub Networking
- Azure DevOps Terraform Complete
- GitHub Bicep Complete
- GitHub Terraform Complete Multi Region
- GitHub Terraform Sovereign Landing Zone
- GitHub Terraform Basic
- GitHub Terraform Hub Networking
- GitHub Terraform Complete
- Local Bicep Complete
- Local Terraform Complete Multi Region
- Local Terraform Sovereign Landing Zone
- Local Terraform Basic
- Local Terraform Hub Networking
- Local Terraform Complete
- Frequently Asked Questions
- Upgrade Guide
- Advanced Scenarios
- Troubleshooting
- Contributing