Releases: 409H/EtherAddressLookup
Blocklist endpoint change + copy changes
Enhancements
- Updated the main blocklist endpoint from Infura to raw.githubusercontent.com as Infura is deprecating those endpoints next month (Huge thanks to Infura for providing them since v1.15.1)
- Updated links from EtherScamDB to CryptoScamDB
- Updated small copy on the popup window footer
- Added link to @CryptoPhishing Twitter feed
Better blacklisting ability
Bug Fixes
- Updated the default node as the Quiknode subscription ran out
New Functionality
- We can now issue blacklists against domains + path, so we can protect you against YouTube livestreams using pre-recorded videos to push trust trading scams and fake wallets.
Mini Block Explorer
Bug Fixes
- Fixed bug that broke RPC node change (#1093)
- Fixed bug that that caused the EAL icon title to be incorrect if you're coming from a domain in your EAL bookmarks (#1092)
- Fixed typo (#1091)
New Functionality
Domain badges + performance update
- Added logic to show a badge on the extension icon to identify trust for the domain (#1083)
- Modified CryptoInfluencers branding to HiveOne (#1085)
- Fixes issue when putting your cursor over a lot of addresses at once #1071 (#1087)
- Ensured 3rd party blacklists don't contain duplicate records to the main EAL blacklist (saving space) (#1087)
- Added logic to notify you if the preferred explorer is pointing to an explorer on a different network to one set on EAL (#1087)
- Added goerli block explorer options
Hotfix v1.19.1 (performance update)
- Modified PhishFort repo link for blacklists
- Added Quiknode affiliate link
- Added link to EtherScamDB
- Removed dead block explorer link
In-extension phishing warning view
Performace update and unminified code (requirement to remain on the Chrome store since the dependancies aren't loaded in via npm or other - new 2019 policy)
- Phishing/Warning views are part of the extension - See #916
- Unminified all the minified-js files
- The web worker js script is only loaded on the Twitter domain (since it's only being used there)
- Set the punycode autoblocker to be disabled by default (RU users were mostly affected with it being enabled by default)
- Modified the warning view to show a GIF on how to disable it.
Hotfix v1.18.2 (performance update)
v1.18.2 is a performance update patch to the Twitter badge functionality. You should start to see less CPU spikes and less lag 👍
- Fixes lag spike when composing a new tweet/reply by not running logic if that is the active element.
- Fixes some CPU spike when running whitelist/blacklist logic by creating a session cache so we don't run the same logic twice a user id
Hotfix v1.18.1
- Added a fix to autofetch the Twitter lists without you opening the extension.
Twitter Badges
(Please also use v1.18.1 - https://github.com/409H/EtherAddressLookup/releases/tag/v1.18.1)
EAL will now put a badge next to each Twitter handle. Green means verified, red is bad! This means at a glance you can see if the handle is trusted by the extension!
CryptoInfluencers has provided us with the top 1,000 Twitter handles with influence in the crypto scene so HUGE shoutout to them!
There are 3 different coloured Twitter badges which you can read about in our wiki.
This feature is enabled by default, but you can toggle it on/off to your liking.

Address book
EAL now has the ability to add labels to addresses!
By going to the "Labels" tab, you can create a label, add a color to the label, and choose which address to associate it with. The labels will be displayed on the address hover box - https://youtu.be/lEX7jR5IV7g
You could plan to color code the labels to have, for example;
- Green labels as your exchange deposit addresses
- Yellow labels as your friends addresses, and
- Blue addresses for community donation addresses!
Thanks to https://chronologic.network for the label feature!
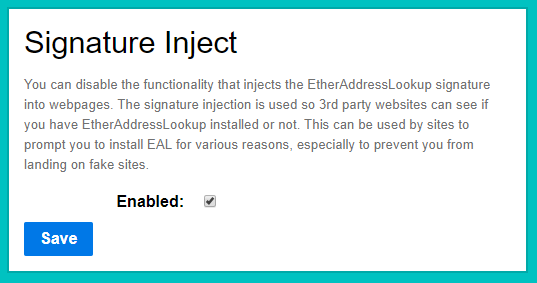
Along with this release, EAL now has the option to inject a signature into the page - which can be toggled off. In coming days we will be releasing a small webpage that will generate a .js file that webmasters can use to prompt users to install EAL if the signature is not injected. This will come in handy for those running domains that are targetted by phishers and have phishing domains blacklisted on the EAL blacklists (including 3rd party lists - iosiro or segasec)