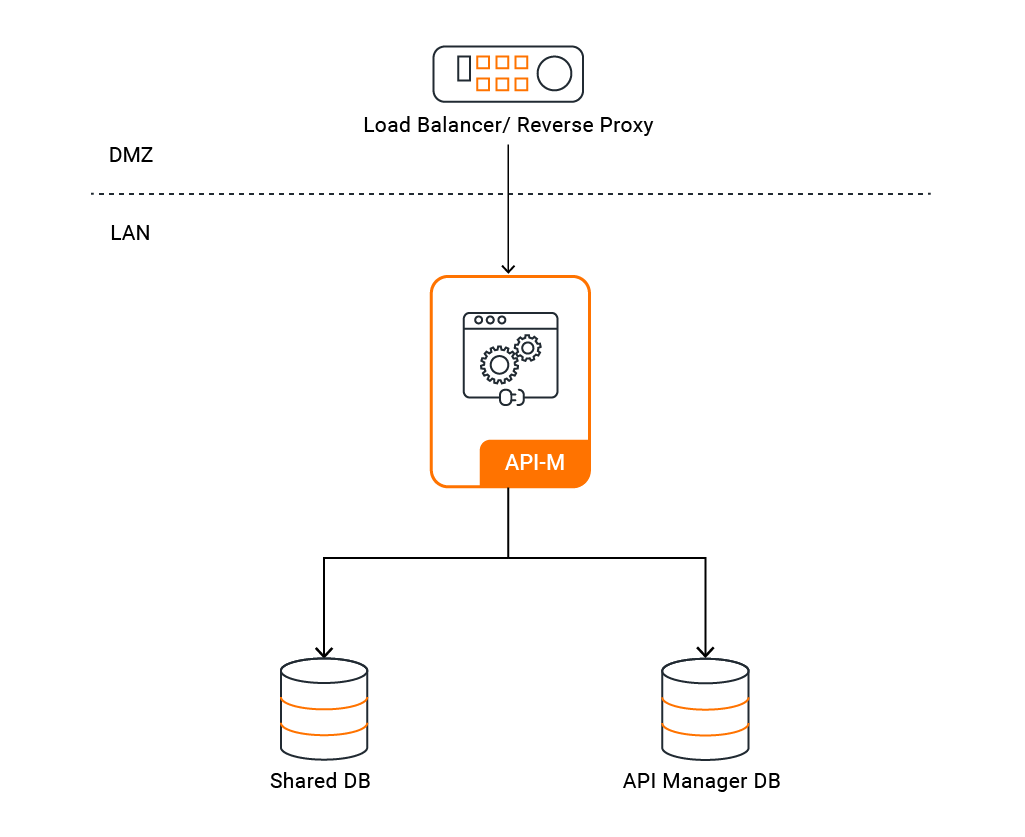
Resources for building a Helm chart for deployment of Single Node API Manager.
For advanced details on the deployment pattern, please refer to the official documentation.
- Prerequisites
- Quick Start Guide
- Configuration
- Runtime Artifact Persistence and Sharing
- Managing Java Keystores and Truststores
- Configuring SSL in Service Exposure
-
WSO2 product Docker images used for the Kubernetes deployment.
WSO2 product Docker images available at DockerHub package General Availability (GA) versions of WSO2 products with no WSO2 Updates.
For a production grade deployment of the desired WSO2 product-version, it is highly recommended to use the relevant Docker image which packages WSO2 Updates, available at WSO2 Private Docker Registry. In order to use these images, you need an active WSO2 Subscription.
-
Install Git, Helm and Kubernetes client in order to run the steps provided in the following quick start guide.
-
An already setup Kubernetes cluster.
-
Install NGINX Ingress Controller.
-
Add the WSO2 Helm chart repository.
helm repo add wso2 https://helm.wso2.com && helm repo update
You can install the relevant Helm chart either from WSO2 Helm Chart Repository or by source.
Note:
NAMESPACEshould be the Kubernetes Namespace in which the resources are deployed.
Install Chart From WSO2 Helm Chart Repository
Helm version 2
helm install --name <RELEASE_NAME> wso2/am-single-node --version 4.2.0-1 --namespace <NAMESPACE>
Helm version 3
-
Deploy the Kubernetes resources using the Helm Chart
helm install <RELEASE_NAME> wso2/am-single-node --version 4.2.0-1 --namespace <NAMESPACE> --create-namespace
The above steps will deploy the deployment pattern using WSO2 product Docker images available in WSO2 Private Docker Registry. Please provide your WSO2 Subscription credentials via input values (using --set argument).
Please see the following example.
helm install --name <RELEASE_NAME> wso2/am-single-node --version 4.2.0-1 --namespace <NAMESPACE> --set wso2.subscription.username=<SUBSCRIPTION_USERNAME> --set wso2.subscription.password=<SUBSCRIPTION_PASSWORD>
If you are using a custom WSO2 Docker images you will need to provide those information via the input values. Please refer API Manager Server Configurations
In the context of this document,
KUBERNETES_HOMEwill refer to a local copy of thewso2/kubernetes-apimGit repository.HELM_HOMEwill refer to<KUBERNETES_HOME>/simple.
git clone https://github.com/wso2/kubernetes-apim.git
Helm version 2
helm install --dep-up --name <RELEASE_NAME> <HELM_HOME>/am-single --version 4.2.0-1 --namespace <NAMESPACE>
Helm version 3
-
Deploy the Kubernetes resources using the Helm Chart
helm install <RELEASE_NAME> <HELM_HOME>/am-single --version 4.2.0-1 --namespace <NAMESPACE> --dependency-update --create-namespace
The above steps will deploy the deployment pattern using WSO2 product Docker images available in WSO2 Private Docker Registry. Please provide your WSO2 Subscription credentials via input values (using --set argument).
Please see the following example.
helm install --name <RELEASE_NAME> <HELM_HOME>/am-single --version 4.2.0-1 --namespace <NAMESPACE> --set wso2.subscription.username=<SUBSCRIPTION_USERNAME> --set wso2.subscription.password=<SUBSCRIPTION_PASSWORD>
If you are using a custom WSO2 Docker images you will need to provide those information via the input values. Please refer API Manager Server Configurations
Note: If you are using Rancher Desktop for the Kubernetes cluster, add the following changes.
- Change
storageClasstolocal-pathinvalues.yaml.- Change
accessModesinPersistent Volume ClaimstoReadWriteOnce.
If you need to enable Choreo Analytics with WSO2 API Manager, please follow the documentation on Register for Analytics to obtain the on-prem key for Analytics.
The following example shows how to enable Analytics with the helm charts.
Helm v2
helm install --name <RELEASE_NAME> wso2/am-single-node --version 4.2.0-1 --namespace <NAMESPACE> --set wso2.choreoAnalytics.enabled=true --set wso2.choreoAnalytics.endpoint=<CHOREO_ANALYTICS_ENDPOINT> --set wso2.choreoAnalytics.onpremKey=<ONPREM_KEY>
Helm v3
helm install <RELEASE_NAME> wso2/am-single-node --version 4.2.0-1 --namespace <NAMESPACE> --set wso2.choreoAnalytics.enabled=true --set wso2.choreoAnalytics.endpoint=<CHOREO_ANALYTICS_ENDPOINT> --set wso2.choreoAnalytics.onpremKey=<ONPREM_KEY> --create-namespace
You will be able to see the Analytics data when you log into Choreo Analytics Portal.
Obtain the external IP (EXTERNAL-IP) of the API Manager Ingress resources, by listing down the Kubernetes Ingresses.
kubectl get ing -n <NAMESPACE>
The output under the relevant column stands for the following.
API Manager Publisher-DevPortal
- NAME: Metadata name of the Kubernetes Ingress resource (defaults to
wso2am-single-node-am-ingress) - HOSTS: Hostname of the WSO2 API Manager service (
<wso2.deployment.am.ingress.management.hostname>) - ADDRESS: External IP (
EXTERNAL-IP) exposing the API Manager service to outside of the Kubernetes environment - PORTS: Externally exposed service ports of the API Manager service
API Manager Gateway
- NAME: Metadata name of the Kubernetes Ingress resource (defaults to
wso2am-single-node-am-gateway-ingress) - HOSTS: Hostname of the WSO2 API Manager's Gateway service (
<wso2.deployment.am.ingress.gateway.hostname>) - ADDRESS: External IP (
EXTERNAL-IP) exposing the API Manager's Gateway service to outside of the Kubernetes environment - PORTS: Externally exposed service ports of the API Manager' Gateway service
API Manager WebSub
- NAME: Metadata name of the Kubernetes Ingress resource (defaults to
wso2am-single-node-am-websub-ingress) - HOSTS: Hostname of the WSO2 API Manager's Gateway (WebSub) service (
<wso2.deployment.am.ingress.websub.hostname>) - ADDRESS: External IP (
EXTERNAL-IP) exposing the API Manager's Gateway service to outside of the Kubernetes environment - PORTS: Externally exposed service ports of the API Manager' Gateway (WebSub) service
If the defined hostnames (in the previous step) are backed by a DNS service, add a DNS record mapping the hostnames and
the external IP (EXTERNAL-IP) in the relevant DNS service.
If the defined hostnames are not backed by a DNS service, for the purpose of evaluation you may add an entry mapping the
hostnames and the external IP in the /etc/hosts file at the client-side.
<EXTERNAL-IP> <wso2.deployment.am.ingress.management.hostname> <wso2.deployment.am.ingress.gateway.hostname>
-
API Manager Publisher:
https://<wso2.deployment.am.ingress.management.hostname>/publisher -
API Manager DevPortal:
https://<wso2.deployment.am.ingress.management.hostname>/devportal
The following tables lists the configurable parameters of the chart and their default values.
| Parameter | Description | Default Value |
|---|---|---|
wso2.subscription.username |
Your WSO2 Subscription username | - |
wso2.subscription.password |
Your WSO2 Subscription password | - |
wso2.choreoAnalytics.enabled |
Chorero Analytics enabled or not | false |
wso2.choreoAnalytics.endpoint |
Choreo Analytics endpoint | https://analytics-event-auth.choreo.dev/auth/v1 |
wso2.choreoAnalytics.onpremKey |
On-prem key for Choreo Analytics | - |
If you do not have an active WSO2 subscription, do not change the parameters wso2.subscription.username and wso2.subscription.password.
| Parameter | Description | Default Value |
|---|---|---|
wso2.deployment.dependencies.mysql |
Enable the deployment and usage of WSO2 API Management MySQL based Helm Chart | true |
wso2.deployment.dependencies.nfsProvisioner |
Enable the deployment and usage of NFS Server Provisioner (https://github.com/helm/charts/tree/master/stable/nfs-server-provisioner) | true |
| Parameter | Description | Default Value |
|---|---|---|
wso2.deployment.persistentRuntimeArtifacts.storageClass |
Appropriate Kubernetes Storage Class | nfs |
wso2.deployment.persistentRuntimeArtifacts.sharedArtifacts.capacity.executionPlans |
Capacity for execution plans shared between the Traffic Manager profile instances | 20M |
wso2.deployment.persistentRuntimeArtifacts.sharedArtifacts.capacity.synapseConfigs |
Capacity for synapse artifacts of APIs shared between the Gateway profile instances | 50M |
wso2.deployment.persistentRuntimeArtifacts.apacheSolrIndexing.enabled |
Indicates if persistence of the runtime artifacts for Apache Solr-based indexing is enabled | false |
wso2.deployment.persistentRuntimeArtifacts.apacheSolrIndexing.capacity.carbonDatabase |
Capacity for persisting the H2 based local Carbon database file | 50M |
wso2.deployment.persistentRuntimeArtifacts.apacheSolrIndexing.capacity.solrIndexedData |
Capacity for persisting the Apache Solr indexed data | 50M |
| Parameter | Description | Default Value |
|---|---|---|
wso2.deployment.am.dockerRegistry |
Registry location of the Docker image to be used to create API Manager instances | - |
wso2.deployment.am.imageName |
Name of the Docker image to be used to create API Manager instances | wso2am |
wso2.deployment.am.imageTag |
Tag of the image used to create API Manager instances | 4.2.0 |
wso2.deployment.am.imagePullPolicy |
Refer to doc | Always |
wso2.deployment.am.livenessProbe.initialDelaySeconds |
Initial delay for the live-ness probe for API Manager node | 180 |
wso2.deployment.am.livenessProbe.periodSeconds |
Period of the live-ness probe for API Manager node | 10 |
wso2.deployment.am.readinessProbe.initialDelaySeconds |
Initial delay for the readiness probe for API Manager node | 180 |
wso2.deployment.am.readinessProbe.periodSeconds |
Period of the readiness probe for API Manager node | 10 |
wso2.deployment.am.resources.requests.memory |
The minimum amount of memory that should be allocated for a Pod | 2Gi |
wso2.deployment.am.resources.requests.cpu |
The minimum amount of CPU that should be allocated for a Pod | 2000m |
wso2.deployment.am.resources.limits.memory |
The maximum amount of memory that should be allocated for a Pod | 3Gi |
wso2.deployment.am.resources.limits.cpu |
The maximum amount of CPU that should be allocated for a Pod | 3000m |
wso2.deployment.am.config |
Custom deployment configuration file (<WSO2AM>/repository/conf/deployment.toml) |
- |
wso2.deployment.am.ingress.management.enabled |
If enabled, create ingress resource for API Manager management consoles | true |
wso2.deployment.am.ingress.management.hostname |
Hostname for API Manager Admin Portal, Publisher, DevPortal and Carbon Management Console | am.wso2.com |
wso2.deployment.am.ingress.management.annotations |
Ingress resource annotations for API Manager management consoles | Community NGINX Ingress controller annotations |
wso2.deployment.am.ingress.gateway.enabled |
If enabled, create ingress resource for API Manager Gateway | true |
wso2.deployment.am.ingress.gateway.hostname |
Hostname for API Manager Gateway | gateway.am.wso2.com |
wso2.deployment.am.ingress.gateway.annotations |
Ingress resource annotations for API Manager Gateway | Community NGINX Ingress controller annotations |
wso2.deployment.am.ingress.websub.enabled |
If enabled, create ingress resource for WebSub service | true |
wso2.deployment.am.ingress.websub.hostname |
Hostname for API Manager Gateway WebSub service | gateway.am.wso2.com |
wso2.deployment.am.ingress.websub.annotations |
Ingress resource annotations for API Manager Gateway WebSub | Community NGINX Ingress controller annotations |
Note: The above mentioned default, minimum resource amounts for running WSO2 API Manager server profiles are based on its official documentation.
| Parameter | Description | Default Value |
|---|---|---|
kubernetes.serviceAccount |
Name of the Kubernetes Service Account to which the Pods are to be bound | wso2am-single-node-svc-account |
-
It is mandatory to set an appropriate Kubernetes StorageClass in this deployment, for persistence and sharing.
-
By default, this deployment uses the
nfsKubernetes StorageClass created using the official, stable NFS Server Provisioner. -
Only persistent storage solutions supporting
ReadWriteManyaccess mode are applicable forwso2.deployment.persistentRuntimeArtifacts.storageClass. -
Please refer to the official WSO2 container guide for advanced details with regards to WSO2 recommended, storage options.
-
By default, this deployment uses the default keystores and truststores provided by the relevant WSO2 product.
-
For advanced details with regards to managing custom Java keystores and truststores in a container based WSO2 product deployment please refer to the official WSO2 container guide.
- For WSO2 recommended best practices in configuring SSL when exposing the internal product services to outside of the Kubernetes cluster, please refer to the official WSO2 container guide.